Table of Contents
- What is Cloud Infrastructure Entitlement Management?
- Key Benefits of CIEM
- Best Practices for Implementing CIEM
- Future Trends in CIEM
Key Takeaways
- Understanding CIEM and its role in cloud security
- Key benefits and features of Cloud Infrastructure Entitlement Management
- Best practices for implementing CIEM in organizations
- Future trends in CIEM and cloud security
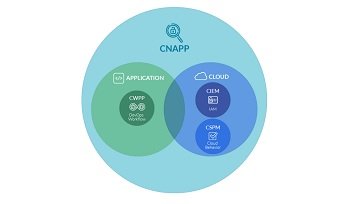
What is Cloud Infrastructure Entitlement Management?
CIEM is an essential component of contemporary cloud security approaches. It revolves around overseeing the privileges and authorizations of individuals who use cloud services. With cloud environments growing in complexity and size, it is crucial to security that only authorized users can access the appropriate resources.
CIEM solutions offer a organized method for managing access in cloud infrastructures. By determining and controlling who is allowed to access different areas of the cloud system, organizations can greatly lower the threat of unauthorized entry and security violations. Maintaining the integrity and confidentiality of data stored in the cloud is dependent on having this level of control. Moreover, automated tools are frequently utilized to simplify and reinforce these procedures, improving both effectiveness and safety measures.
In addition, CIEM tackles a key issue in cloud security: the constant and temporary state of cloud resources and services. Conventional approaches to entitlement management are typically inflexible and struggle to adjust rapidly to changes, while CIEM solutions are created to be adaptable and prompt in their response. This is why CIEM is crucial for all organizations seeking to uphold strong security in a cloud-focused environment.
Key Benefits of CIEM
One of the primary benefits of implementing CIEM is enhanced security. Organizations can better prevent unauthorized users from accessing sensitive information by clearly defining and enforcing access permissions. This is critical today, where data breaches can have severe financial and reputational impacts. A breach can lead to hefty fines, erode customer trust, and damage a company’s reputation irreparably.
Additionally, CIEM helps improve compliance with various regulatory requirements. Many industries are subject to strict regulations regarding data access and protection. Implementing a comprehensive CIEM strategy ensures that an organization can demonstrate compliance with these regulations, thereby avoiding fines and other penalties. Organizations can also simplify audit processes, as CIEM provides a clear record of who has access to each resource and why.
Besides security and compliance, CIEM provides better visibility into cloud activities. According to a report on cloud visibility, having a clear view and better control over cloud infrastructure makes it easier to manage and secure. This visibility helps organizations identify potential security issues before they become critical problems, enabling more proactive management and response.
Furthermore, CIEM enhances operational efficiency by manually reducing the administrative burden of managing entitlements. Automated processes can handle repetitive tasks and ensure policies are consistently applied across the entire cloud environment.
Best Practices for Implementing CIEM
- Assess Your Current Setup: Begin by conducting a thorough review of your existing cloud infrastructure to gain an understanding of the current permissions and entitlements. This initial assessment will provide a baseline to build a more secure and efficient entitlement management strategy. Identifying any existing gaps or vulnerabilities early on is critical to developing an effective CIEM implementation plan.
- Define Clear Policies: Establish clear, well-documented entitlement policies that specify who can access resources, under what conditions, and why. These policies must be in accordance with the organization’s security goals and clearly communicated to all parties involved. Clear guidelines aid in avoiding misconfigurations and guaranteeing that every user comprehends their access rights and duties.
- Continuous Monitoring: Implement continuous monitoring to identify and remediate unauthorized access or anomalies promptly. Regular audits and real-time monitoring tools are critical components of a robust CIEM strategy, helping to ensure that entitlements remain appropriate and secure over time. Continuous monitoring enables organizations to identify and react to potential security incidents at a faster pace, decreasing the likelihood of data breaches.
- Automate Management: Use automation tools to manage entitlements as your cloud environment evolves dynamically. Automation can reduce human error, ensure compliance with policies, and manage the scalability of cloud resources more efficiently. By leveraging automation, organizations can more effectively adapt to changes in the cloud environment and maintain security. Automation also enables IT teams to implement changes more quickly and consistently, enhancing overall security posture.
Future Trends in CIEM
CIEM is progressing towards becoming increasingly vital in cloud security. Emerging trends include utilizing AI and ML to forecast cloud permissions management. These technologies have the capability to forecast potential security threats and adjust access levels accordingly, providing a proactive approach to cloud security. AI and ML are capable of examining large sets of data to uncover patterns and irregularities that may signal possible security threats.
In addition, as cloud infrastructures expand, it will be crucial to merge CIEM with other security solutions like Security Information and Event Management (SIEM) platforms. This comprehensive strategy guarantees a complete perspective on security across different cloud platforms and services, enhancing protection against possible threats. By merging CIEM and SIEM systems, a comprehensive understanding of security incidents can be achieved, enhancing monitoring and response efficiency.
Moreover, the growing utilization of cloud-native apps and services is expected to increase the implementation of advanced CIEM solutions. Managing the unique entitlement requirements of these applications can be difficult with conventional tools. Sophisticated CIEM solutions will be needed to handle these challenges and guarantee proper management of entitlements in fluid, cloud-native settings.